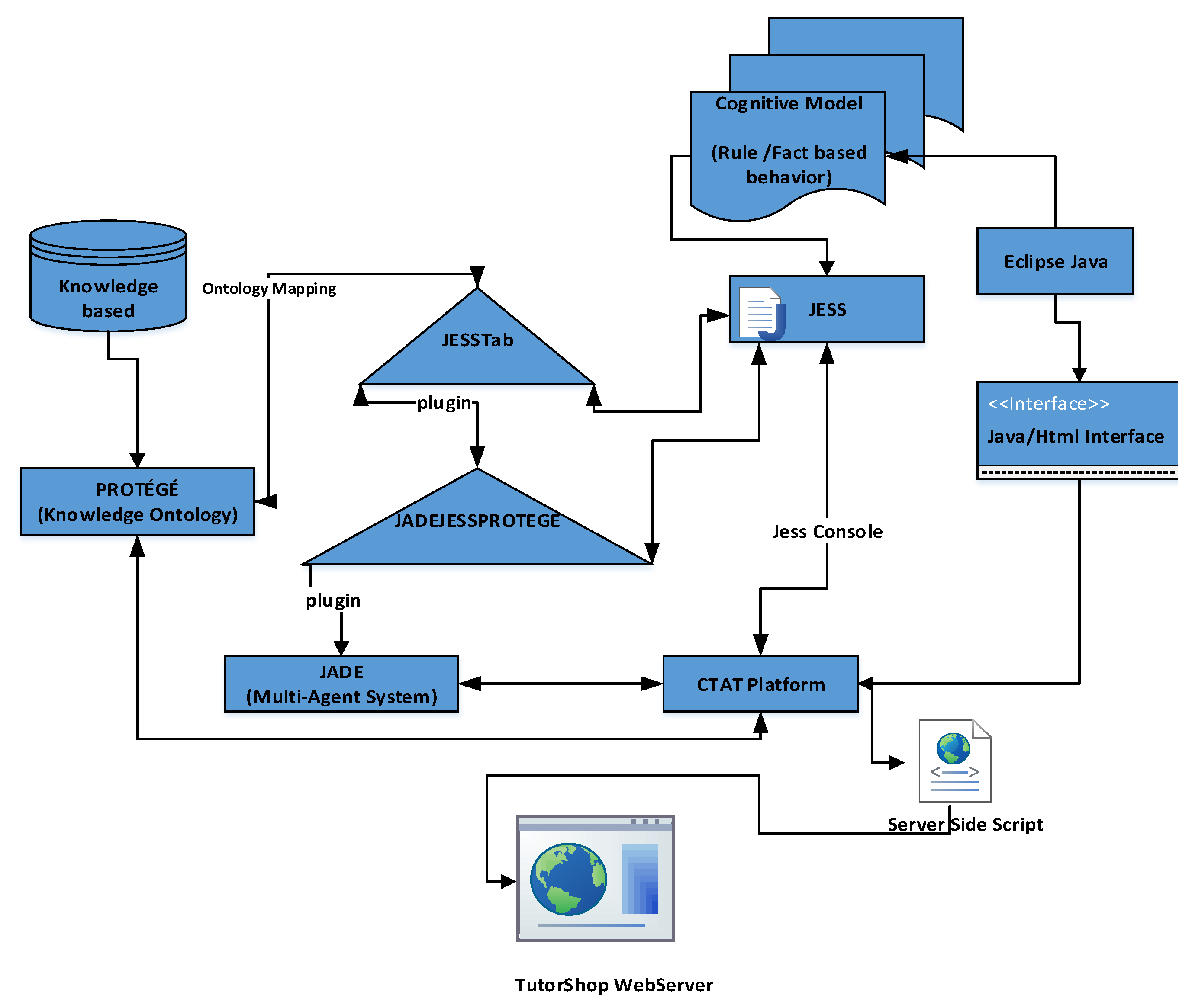
Applied Sciences | Free Full-Text | PACA-ITS: A Multi-Agent System for Intelligent Virtual Laboratory Courses | HTML

PDF) BIOMETRIC APPLICATION OF INTELLIGENT AGENTS IN FAKE DOCUMENT DETECTION OF JOB APPLICANTS | International Journal of Computer Science, Engineering and Information Technology (IJCSEIT) - Academia.edu
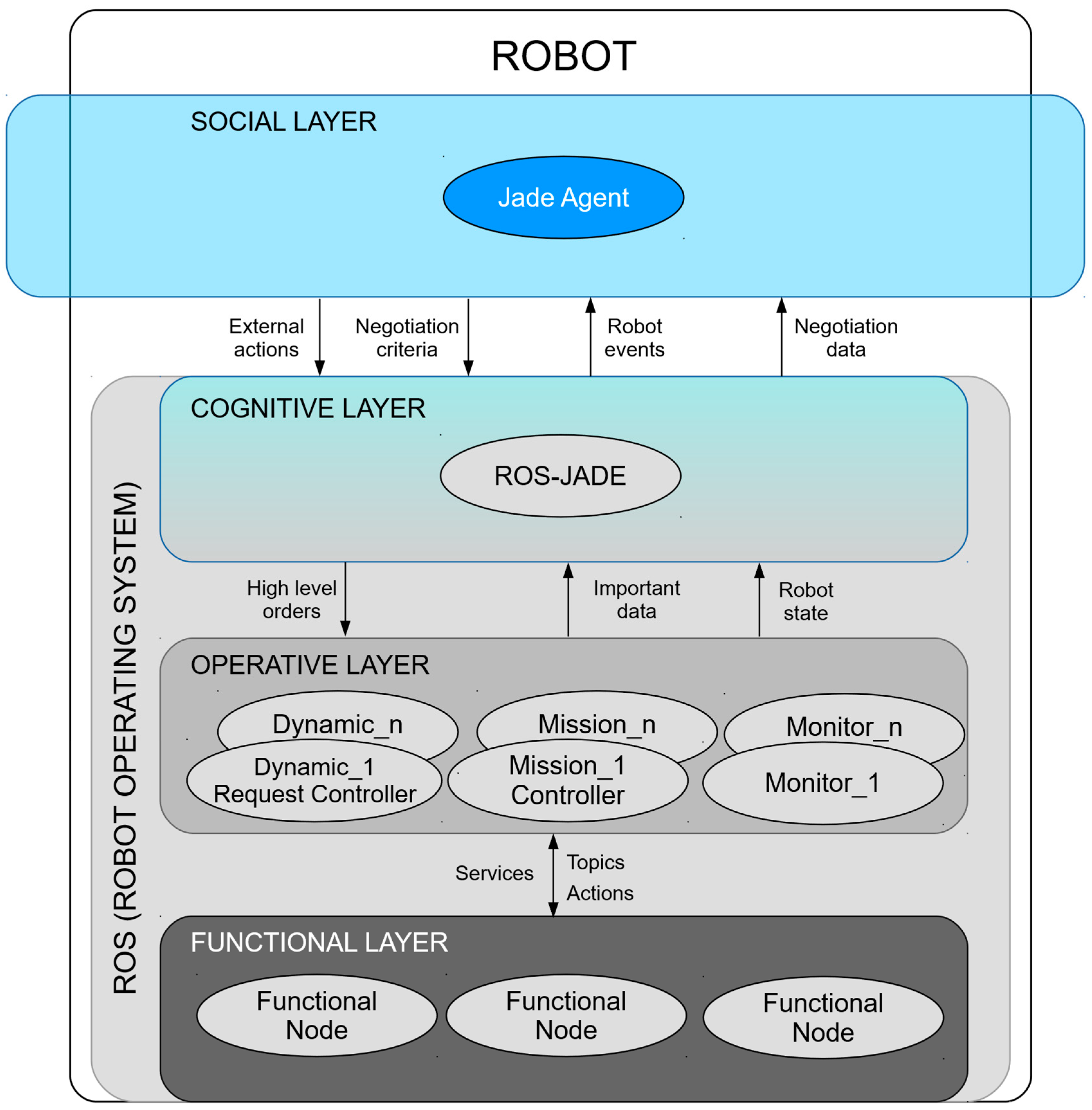
Sensors | Free Full-Text | A Generic Multi-Layer Architecture Based on ROS- JADE Integration for Autonomous Transport Vehicles
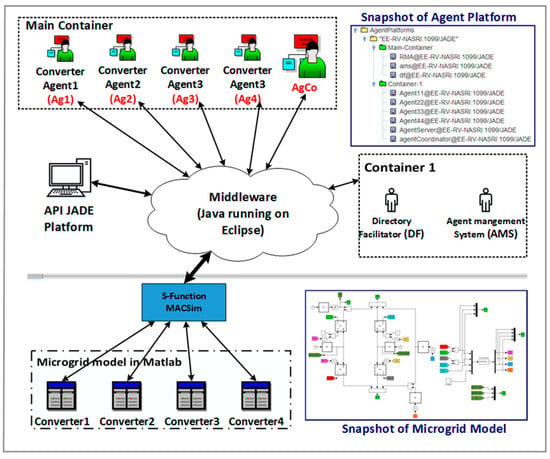
Electronics | Free Full-Text | Agent-Based Coordinated Control of Power Electronic Converters in a Microgrid
Automated cryptocode generator is helping secure the web | MIT News | Massachusetts Institute of Technology

JADE implemented mobile multi-agent based, distributed information platform for pervasive health care monitoring - ScienceDirect
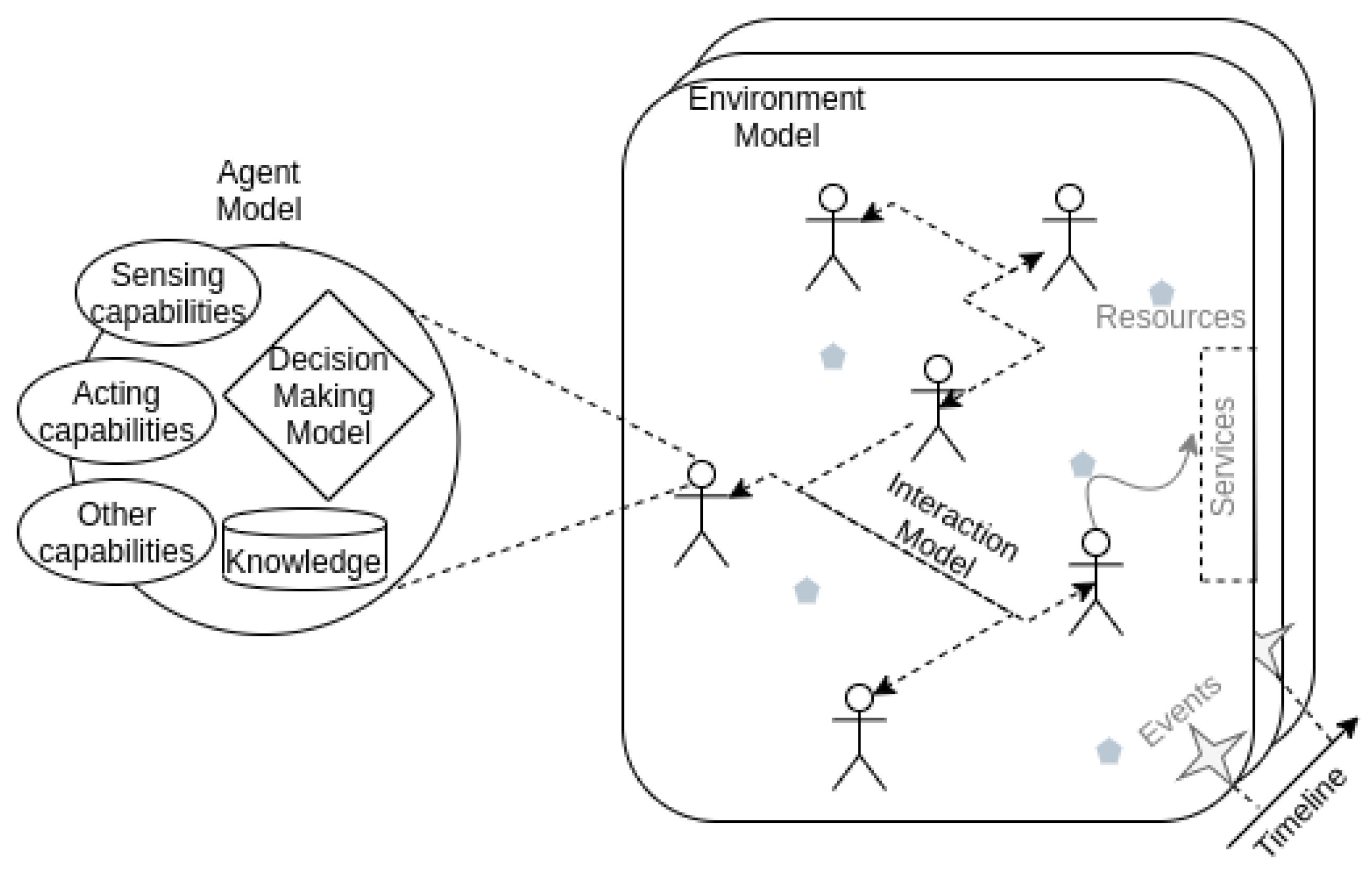
Processes | Free Full-Text | Multi-Agent Systems and Complex Networks: Review and Applications in Systems Engineering | HTML
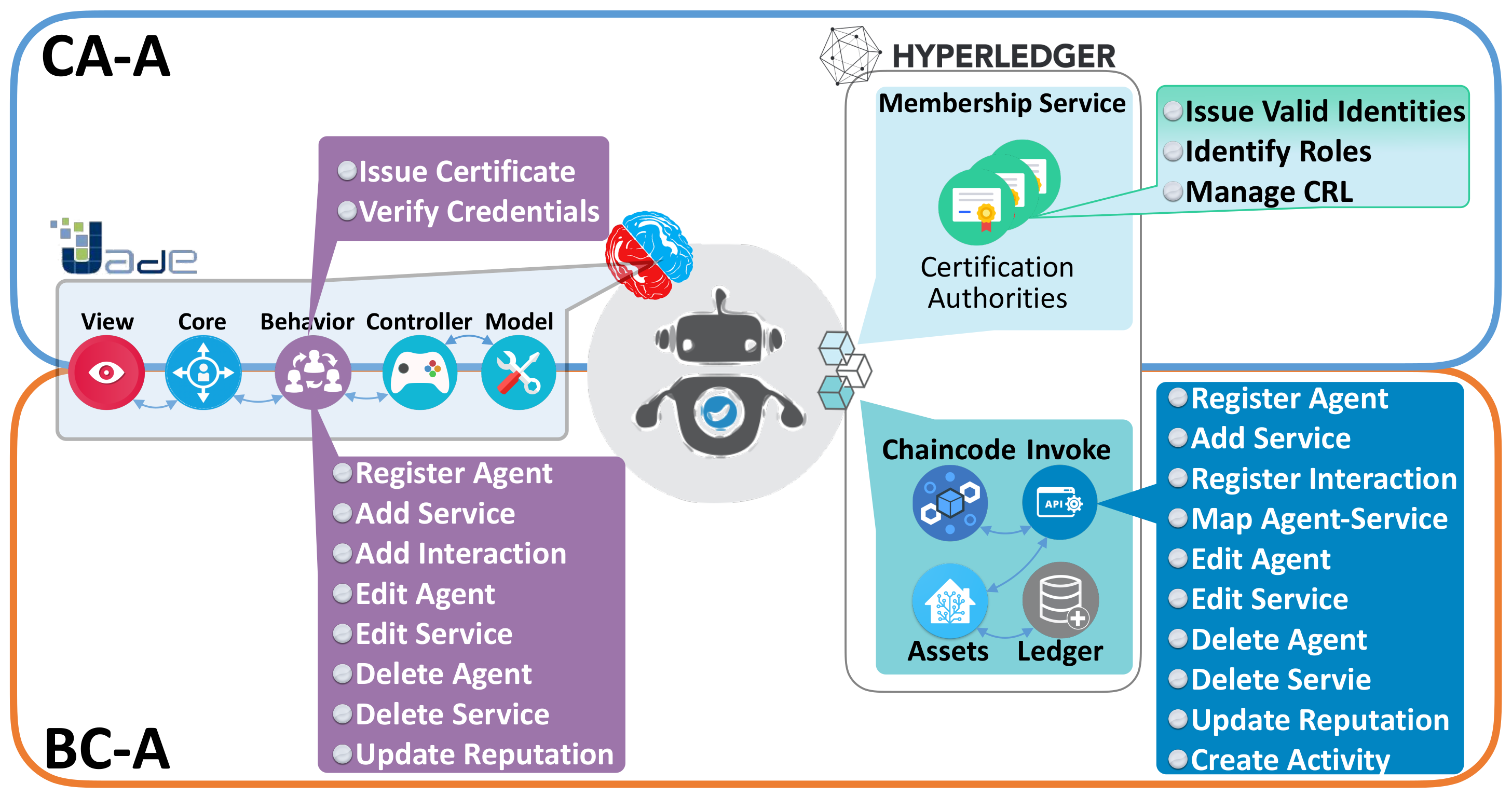
Information | Free Full-Text | The Good, the Bad, and the Ethical Implications of Bridging Blockchain and Multi-Agent Systems | HTML










![PDF] Agent Based Secured e-Shopping Using Elliptic Curve Cryptography | Semantic Scholar PDF] Agent Based Secured e-Shopping Using Elliptic Curve Cryptography | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/47bf34fbe8c2b81240b509b4fb88b6757fbbe00f/3-Table1-1.png)
![PDF] Mobile Agent Data Security using Triple Data Encryption Standard | Semantic Scholar PDF] Mobile Agent Data Security using Triple Data Encryption Standard | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/f3b33bc6c1297863ed2235a3a07e1ef30f06ef75/5-Figure3-1.png)